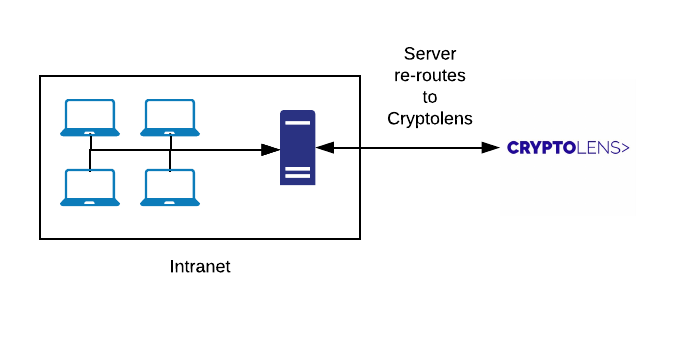
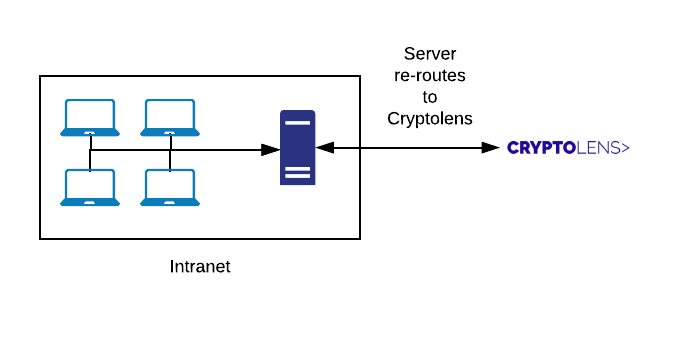
Node.js software licensing
Today we have released a client library for Node.js, which can be installed quite easily using the command below:
npm install cryptolensOnce it’s installed, you can verify a license key using the code below:
const Key = require('cryptolens').Key;
var RSAPubKey = "{Your RSA Public key, which can be found here: https://app.cryptolens.io/User/Security}";
var result = Key.Activate(token="{Access token with with Activate permission}", RSAPubKey, ProductId=3349, Key="GEBNC-WZZJD-VJIHG-GCMVD", MachineCode="test");
result.then(function(license) {
if (!license) {
// failure
return;
}
// Please see https://app.cryptolens.io/docs/api/v3/model/LicenseKey for a complete list of parameters.
console.log(license.Created);
});If you want to load a license key (eg. for offline activation), you can use LoadFromString method available in the Helpers namespace. You can read more about it here.
Disclaimer: this is not an April joke, we support Node.js for real 🙂